Do you realize that security has become a major priority for companies undergoing digital transformation? Microsoft Azure continues to improve its cloud task orchestration capabilities, with the goal of making Azure the most comprehensive solution available.
Microsoft Azure, being one of the leading cloud providers, offers a variety of services and capabilities out of the box to ensure comprehensive security for workloads hosted on its platform. Here are 10 Azure security best practices checklist that should be the first step in your cloud security journey.
The topics covered in this blog are:
Why Azure Security?
Azure is one of the greatest and most popular cloud computing service providers. Storage, databases, networks, and many other services function in tandem in Azure. Every day, an organization keeps and accesses confidential information. Someone cannot infiltrate a company’s systems, seize all of the controls, and release secret information. Azure offers a wide range of services to help you strengthen and secure your network. It will notify you immediately if there is a significant problem, but there are several steps you can work on to assure double security in Azure.
Here we are listing the Top 10 Microsoft Azure Security Best Practices to safeguard companies.
Top 10 Microsoft Azure Security Best practices
1. Using Dedicated Workstations
Users that use accounts with high fees are frequently targets of cyber assaults. However, other activities can jeopardize network security, such as checking e-mail and accessing the Internet.
These are vulnerable to cyber threats such as Malware and Ransomware, which could allow hackers to get access to your company. Microsoft Azure has brought up Privileged Access Workstations to address this issue (PAWs).

Azure security best practices checklist provides a secure operating system for sensitive tasks insulated from external threats. The separation of these workstations and common-use devices provides excellent protection against phishing attempts, operating system flaws, and application vulnerabilities. This solution adheres to Microsoft Azure security best practices, which recommend that normal users be separated from administrators’ accounts, which must be nominative.
2. Key Management
All sensitive data, such as passwords, is encrypted into keys. These are far more secure and can be used as a password in any security check. Azure security best practices checklist includes key management. To prevent misuse and loss, keys must be securely encrypted and safeguarded. To protect cloud data, secure key management is essential.

Azure Key Vault enables you to securely store encryption and secure keys in an HSM (Hardware Security Modules). Microsoft uses HSM to process keys in accordance with the FIPS 140-2 Level 2 standard. Monitor key usage by sending logs to Azure or Security Information and Event Management for improved threat detection (SIEM)
3. Restrict User Access
Organizations can achieve test agility and development by using the Azure security best practices checklist for development environments and laboratories by removing delays caused by material, equipment, and hardware supply.
The popular DevOps methodology can accidentally expose a company to internal threats. Indeed, DevOps may be overly generous with rights allocation due to a lack of Azure expertise or a desire to hasten its implementation. Some users are given significantly more access rights than they need.

Azure Role-Based Access Control is used by the Azure DevTest Labs service (RBAC). It enables a team’s responsibilities division to grant only the level of access required for users to do their jobs. This service has pre-defined roles (owner, lab user, and collaborator). It can assign rights to external partners.
Check Out: Our blog post on Azure Certification Path
4. Leverage Security Center
The Azure Security Center provides native cloud security posture monitoring, which monitors deployments in real-time and alerts any departures from security best practices. Azure security best practices checklist also makes threat avoidance suggestions to lower the attack surface. The service is auto-provisioned with Azure resources, which means there is little to no overhead.
Azure Security Center enables uniform security across numerous environments by allowing security policies to apply across subscriptions, management groups, or tenants. The results of the security assessments conducted by the center are provided as a secure score that quantifies your security posture.

Similarly, the assessments’ security controls are based on guidelines from the Center for Internet Security (CIS) and the National Institute of Standards and Technology (NIST) (NIST). For discovered vulnerabilities, Azure Security Center also gives actionable advice and remedial methods; the remediation process can be human or automated using tools like Logic App.
5. Encrypt Virtual Disks and Disk Storage
By relocating a drive, Azure Disk Encryption minimizes the possibility of data theft or unauthorized access. Azure security best practices checklist includes other security protections. It can be bypassed by connecting the disc to another system. Disk Encryption encrypts the operating system and data drives using BitLocker on Windows and DM-Crypt on Linux.

To control and manage encryption keys, Azure Disk Encryption is connected with Key Vault. Standard virtual machines and virtual machines with premium storage can use it. Data at rest is protected with Azure Storage Services encryption. If turned on in the storage account, it automatically encrypts data in Azure as it is written and then decrypts it when the user wants to access it.
6. Secure with Microsoft SQL Server
Microsoft SQL Server is one of the most widely used services among companies. Azure identifies a variety of risks and assaults, like SQL injection and other vulnerabilities, but you can make it even stronger by periodically setting and monitoring SQL Server Firewall.

It is one of the popular Azure security best practices checklist. Make your SQL Server Firewall policy more robust and robust, and keep track of all security logs, information misuse, and breach alerts.
Also Check: Azure Data Factory Interview Questions and Answers
7. Using Multiple Authentication
We recommend using multiple authentications to secure your Microsoft Azure account. Multiple authentications are an additional authentication mechanism to the password. It helps to reduce the possibility of a foreign person gaining access after a password has been stolen.

Azure Multi-Factor Authentication helps safeguard data and application access while providing a simple authentication method to satisfy user demand. Azure security best practices checklist delivers strong authentication through a series of easy tests, including a phone call, SMS, and mobile app notification. Users can select their preferred technique.
8. Control and Limit the Network Access to Microsoft Azure
Protecting systems that are accessible via the Internet is another popular Azure security best practices checklist. The RDP port is open by default for any new Windows virtual machine deployment; the SSH port is open for each new Linux virtual machine deployment. In order to limit the possibility of illegal access, you must take necessary precautions.
Microsoft Azure supports the use of Network Security Groups (NSG). NSGs restrict access from all networks to the only required access points when using Azure Resource Manager for deployment (RDP or SSH).

You should configure a site-to-site VPN from your local network. The local network is extended to the cloud using a site-to-site VPN. It makes network security groups more useful because they can be configured to prevent access from sites outside the local network. For administration, it is suggested that you connect to the Azure network using a VPN.
Finally, the point-to-site option is available for administrators who want to administer systems that do not require access to local resources. These systems can have their own Azure virtual network. Administrators can attach to the Azure-hosted environment through a VPN.
9. Cloud Storage Account Security
You should configure every storage account to employ blob encryption, file encryption, and secure transmission wherever possible.
To reduce the danger of access keys being compromised, one should regenerate account keys on a regular basis. Shared Access Signatures should only be used for secure transfers and should have an expiration time of no more than eight hours to ensure that access is not granted indefinitely.

One should audit the Blob or file container public access to verify that it is only used in circumstances like public websites. Tripwire Configuration Manager can be used to automatically enforce privacy settings and audit public access to storage containers.
10. Use a WAF with ATM
The Azure Web Application Firewall (WAF) service is built on top of the Application Gateway service and protects Azure SQL databases from OWASP 3.0 assaults. Azure security best practices checklist includes lowering the public internet access of your components to reduce the risks of an attack.
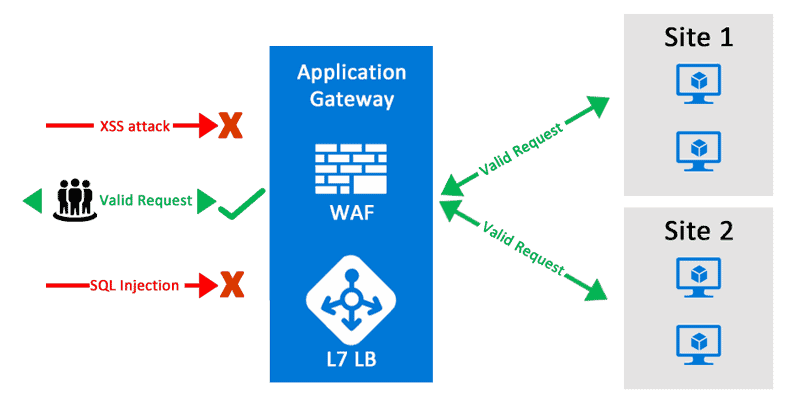
If you don’t want your app to be viewed abroad, use a geolocation filter in Azure Traffic Manager (ATM). As a result, set up settings on your ATM to permit only certain types of traffic while excluding undesired or overseas traffic. Finally, configure your Web Application Firewall to only accept Azure Traffic Manager traffic (ATM).
Conclusion
Multiple tools and services available natively on the platform allow Microsoft Azure Cloud Services to secure cloud-hosted applications. Microsoft’s “assume breach” strategy assists you in ensuring a secure hosting environment with customizable restrictions.
You can use a continuous monitoring solution that checks the good IaaS provider security standards is the best method to assure Cloud Workload security. We have shared the Azure security best practices checklist to start a good point for a security strategy. Companies need a continuous monitoring system to address the security needs of a continually changing environment.
FAQs
Q1. What are Azure security components?
Azure security components refer to the various features and services in Microsoft Azure that contribute to the overall security of the platform. These components include Azure Active Directory, Azure Security Center, Azure Firewall, Azure Sentinel, Azure Key Vault, and more.
Q2. Who is responsible for security in Azure?
While Microsoft Azure ensures the security of its underlying infrastructure, the responsibility for security in Azure is shared between Microsoft (the cloud provider) and the customer (the organization using Azure). Microsoft is responsible for the security “of” the cloud, including physical security, network infrastructure, and platform security. The customer is responsible for the security “in” the cloud, which involves securing their applications, data, user access, and compliance with best practices.
Q3. Why are security best practices important in Microsoft Azure?
Security best practices are crucial in Microsoft Azure to protect data, applications, and resources from various threats and vulnerabilities. They help prevent unauthorized access, data breaches, and service disruptions. Following security best practices ensures the confidentiality, integrity, and availability of your Azure environment, safeguards sensitive information, and reduces the risk of security incidents and compliance violations.
Q4. What are the key security challenges in Azure and how can best practices address them?
Key security challenges in Azure include identity and access management, network security, data protection, threat detection, and compliance. Best practices address these challenges by recommending measures such as strong authentication, role-based access control, network segmentation, encryption, monitoring, and adherence to compliance frameworks like Azure CIS Benchmarks or Azure Security Center recommendations.

