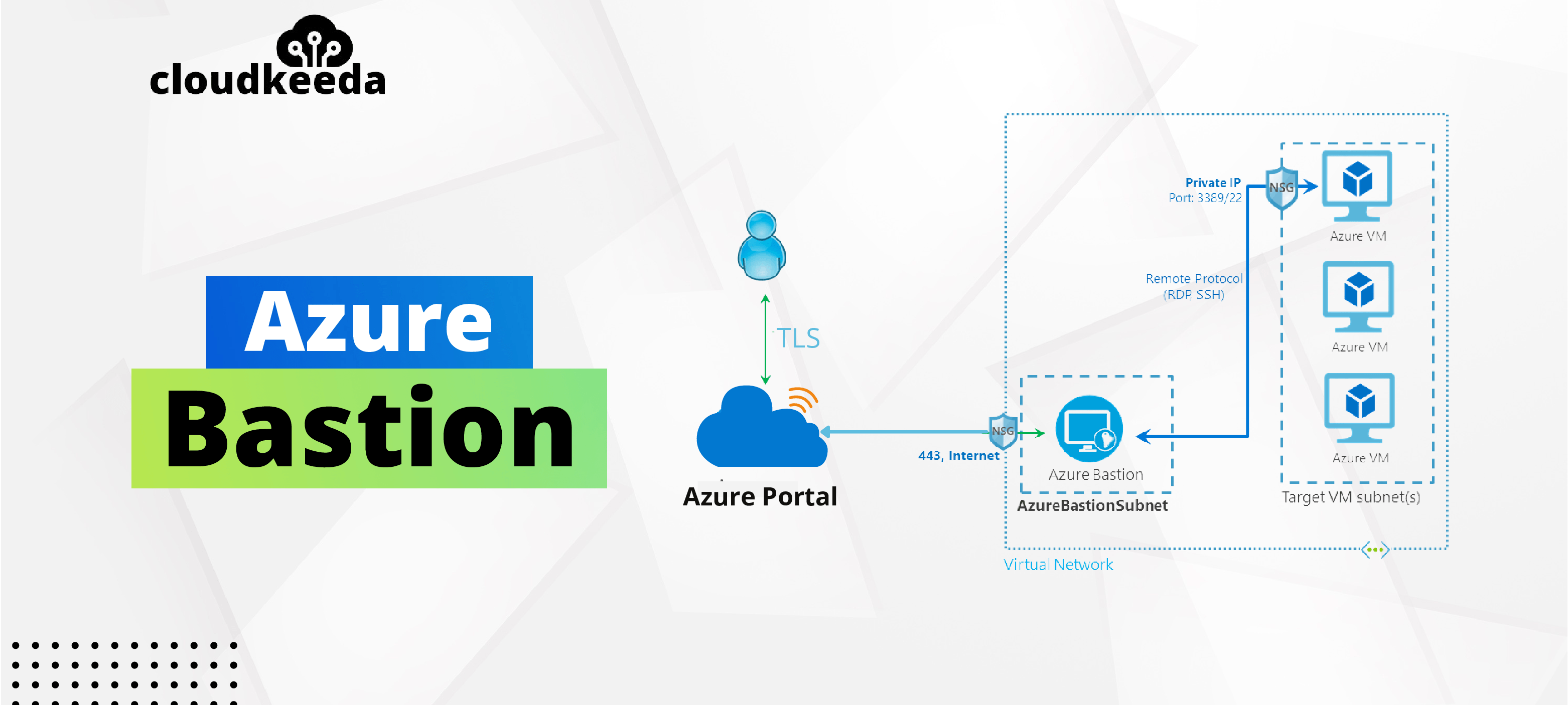
Azure Bastion is a fully managed PaaS service provisioned inside your virtual network. Azure Bastion allows you to connect to a virtual machine using your browser and the Azure portal. Azure Bastion provides secure RDP and SSH connectivity in the virtual network to all the VMs in which it is provisioned.
The topics covered in this blog are:
- What is Azure Bastion?
- Azure Bastion Architecture
- Why do we use Azure Bastion?
- How Azure Bastion Works?
- Azure Bastion Features
- How to Configure Azure Bastion?
- Connect to the Virtual Machine
- Azure Bastion Pricing
- Conclusion
- FAQs
What is Azure Bastion?
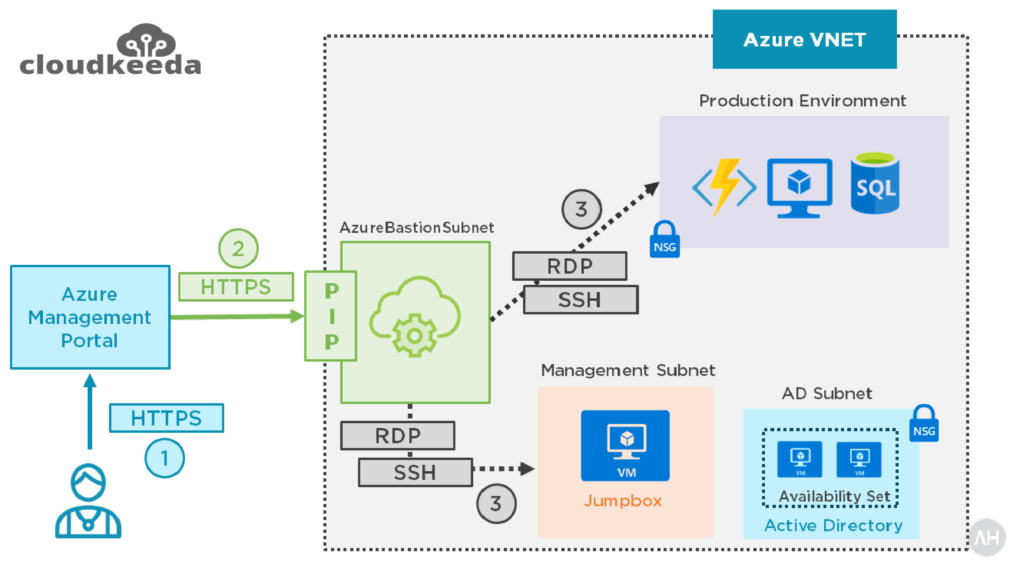
Azure Bastion provides secure RDP/SSH connectivity to your Virtual Machines directly from the Azure portal. In a general RDP connection, a public IP is needed to configure a virtual machine exposed to the world, and that the client machine uses IP to connect and login to the virtual machine. When you connect via Azure Bastion, your VMs do not need an agent or public IP address. Azure Bastion is used to prevent our virtual machines from exposing RDP and SSH ports to the outside world while still allowing secure RDP and SSH connections.
Azure Bastion Architecture
Azure Bastion supports virtual network peering. Specifically, Azure Bastion manages RDP/SSH connectivity to virtual machines that are created on the local virtual networks. RDP and SSH are two of the most common ways through which we can connect to our workloads running in Azure. Due to protocol vulnerabilities sometimes, we expose our RDP/SSH ports over the Internet, which is not desirable and is seen as a large danger surface. You may limit the danger surface by deploying bastion hosts (also known as jump-servers) on the public side of your perimeter network. Bastion host servers are designed to resist intrusions.

Source: Microsoft
Here’s how the connection works:
- You use any browser to connect to the Azure management interface through HTTPS, and then you pick a virtual machine to connect to.
- The Azure portal now connects to the Azure Bastion service on port 443, using a private IP.
- You get a new session in your browser and inside your network using RDP or SSH, you can browse the desktop of the virtual machine and any other VMs.
Also Check: Azure Data Factory Interview Questions
Why do we use Azure Bastion?
In general, we use two methods for connecting Azure VMs, which are stated below:
- Connect using Public IP
- Connect using Jump Box
In both methods, we have to conduct some network hardening and enable just-in-time access, which includes additional expenses. To remove all these efforts, we use Azure Bastion, which allows us to connect all the Azure Virtual Machines without exposing them over the internet.
Method 1: When we use the public Internet to access VMs, the traffic flow is shown below.
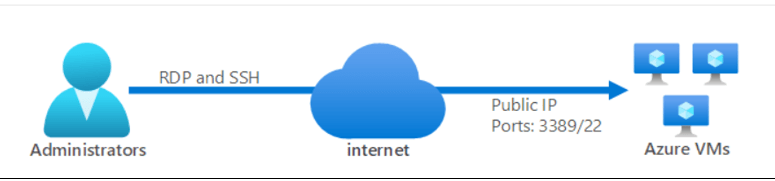
Source: Microsoft
Method 2: When we use Azure Bastion to access VMs, the traffic flow is shown below.

Source: Microsoft
Also Read: Our blog post on Azure Certification Path
How Azure Bastion Works?
Before I describe how Azure Bastion works, I’d want to go through how things have functioned in the past and why you would want to adopt it. Typically, you have a VNET inside Azure and your resources are distributed over one or more subnets.
You may have one or more jump boxes or bastion hosts that contain all your remote administration tools, and they are used to do your administrative tasks. You might also have a hybrid connection with your on-premises network and use Point-to-Site VPN to access your VNET when you are outside of the office, which is the ideal situation.

However, you may have your jump box host configured with a public IP that is accessible from the internet, and you connect to the jump box via RDP and SSH for various reasons. You can use the jump box host to connect to additional resources after connecting to it.
This means that a malicious person might use port scanning to determine your jumpbox’s public IP and then perform a brute force assault to hack it. As a best practice, you should establish a network security group to control which ports and source IP addresses are permitted to connect.
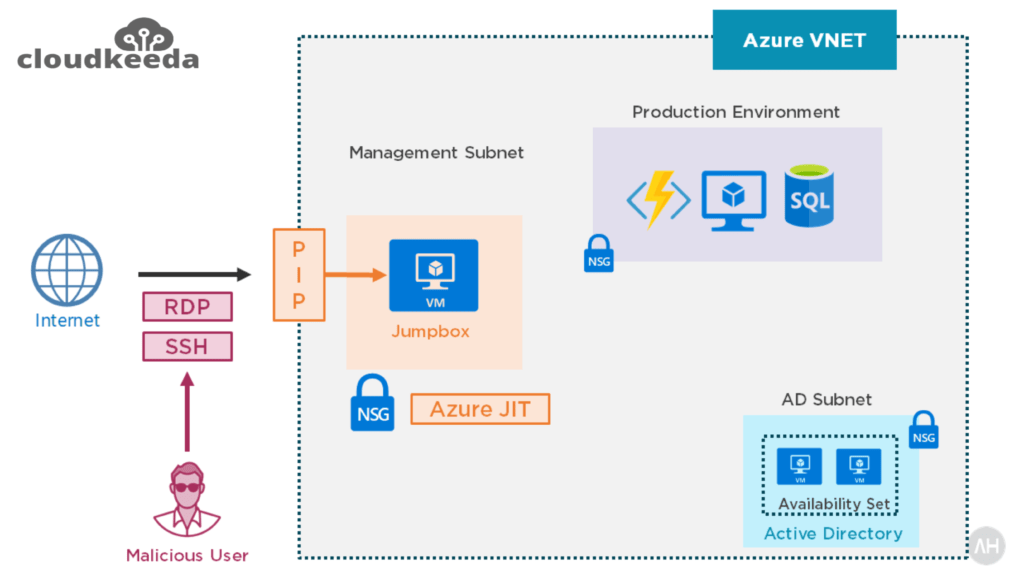
However, your public IP address is still accessible. A preferable option would be to delete this public IP address from your VNET so that you don’t expose both RDP and SSH and decrease your VNET’s attack surface.
Now your jumpbox host does not have any public IP addresses, and you set up an Azure bastion solution that resides on its own managed subnet and exposes a public IP address. However, this IP address does not support RDP or SSH connections. It only allows SSL connections.
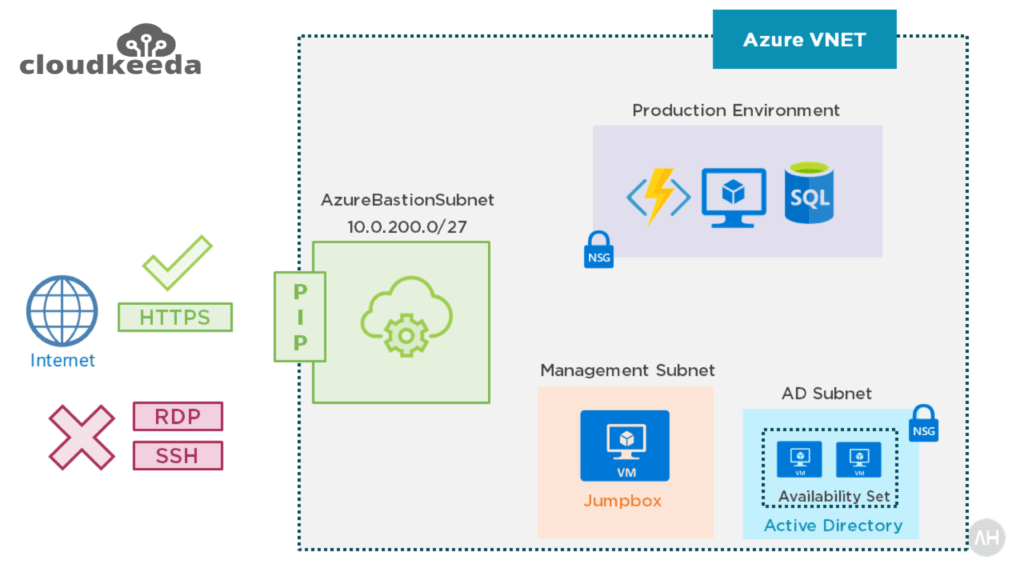
Consider the Azure bastion a proxy. It accepts connections from the internet through SSL and connects you to your VMs via RDP and SSH. It also seems to be a Remote Desktop Gateway solution. You connect from a browser to a gateway, which returns your RDP connection to the browser.
Read More: About Azure Data Factory.
Azure Bastion Features
- Reliable and secure RDP and SSH access to your virtual machines.
- Azure Bastion employs an HTML5-based web client that is transmitted to your local device automatically. This makes firewalls and other security rules extremely simple to handle.
- Azure Bastion connects to your Azure virtual machine through RDP or SSH using the VM’s private IP address. You don’t need a public IP address on your VM.
- Azure Bastion sits at the edge of your virtual network, so you don’t have to worry about hardening each virtual machine in it. By keeping the Azure Bastion constantly up-to-date, the Azure platform safeguards you against zero-day vulnerabilities.
How to configure Azure Bastion?
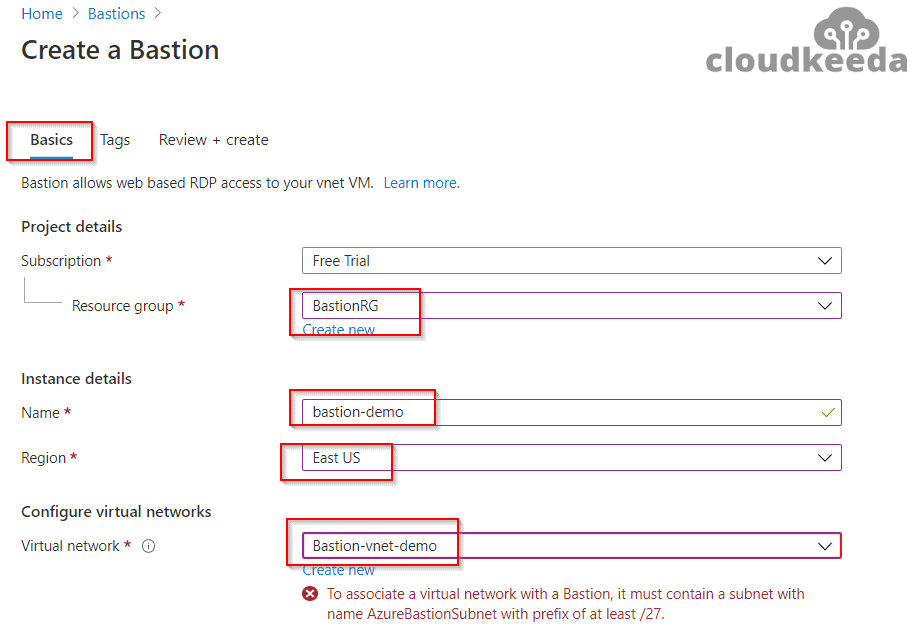
1. Log in to your Azure Portal and type “Bastion” into the search box. As you scroll through the results, click the Create button when you find Bastion with Microsoft as its publisher.
2. Enter all the required fields, such as subscription, instance name, resource group, virtual network, and the region name as well.
3. When you get to the Subnet option, choose Manage Subnet Configuration.

4. Now, click on Add Subnet and establish a subnet with the name AzureBastionSubnet with a prefix of /27 or bigger. Make sure you only use this name.
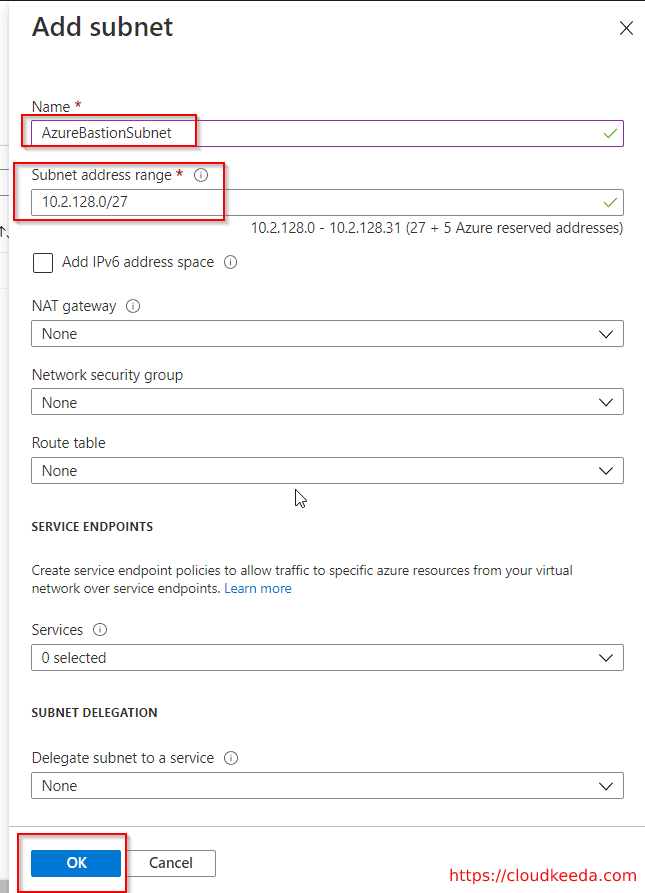
5. Now, click on OK and select your subnet on the Bastion creation page. Now there are two options: creating a new public IP address or using an existing one.
6. If you choose the first option, which is “create a new public IP address,” then provide a name and use the Standard SKU option.

7. Then finally, click on the Review+Create button and then click on Create after the validation process.
Check Out: What is Microsoft Azure?
Connect to the Virtual Machine
1. Go to the Virtual Machines in your portal and then select the newly created bastion, and after that, click on Connect > Bastion in the Overview section.
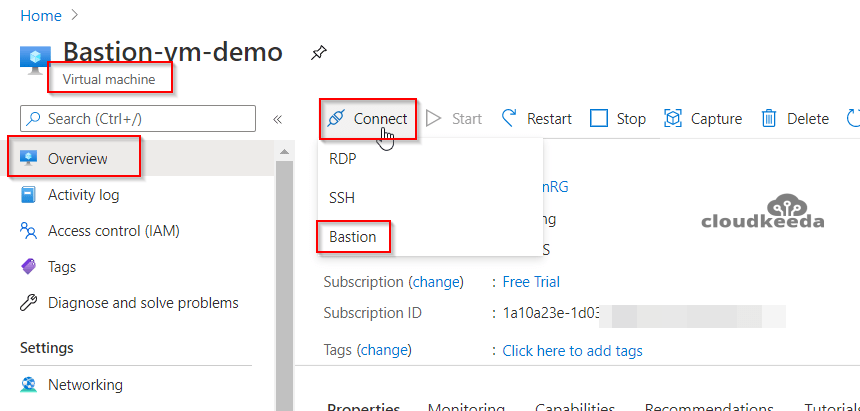
2. Now, click on the “Use Bastion Button” and enter your required credentials to log into it.
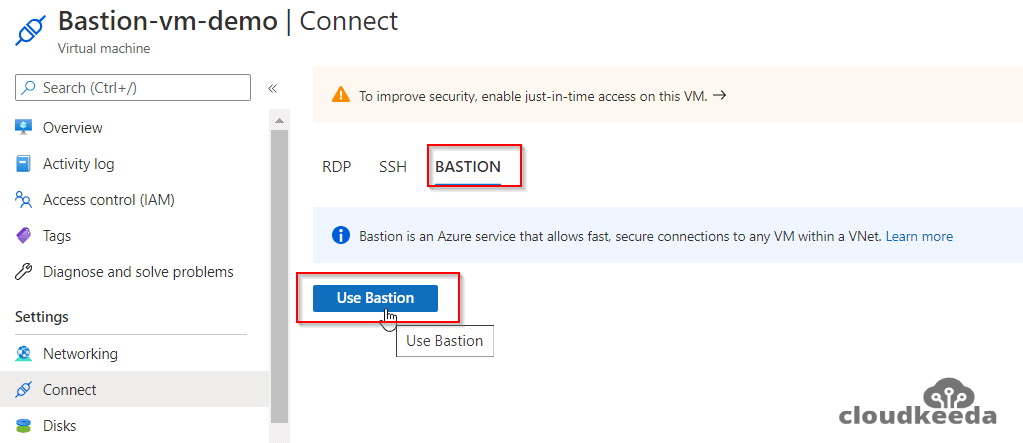
Now a new browser window appears with the VM on that tab.
Also Check: Our blog post on Azure Traffic Manager.
Azure Bastion Pricing
Fixed charges: This is an hourly price for installing the service.
Outbound data transfer charges: This fee is calculated depending on the total amount of data sent outward.
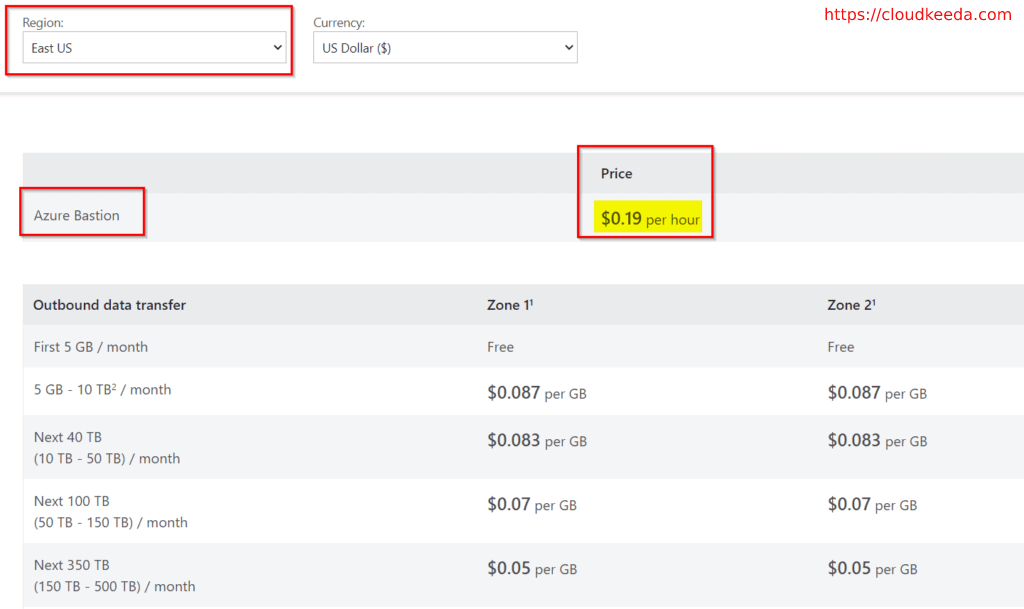
Check Out: Official Pricing Document.
Conclusion
The Azure Bastion Service has a number of useful features, such as SSH and RDP connections, no public IP address needed, and so on. Because of these capabilities, Bastion is a useful solution for connecting to an Azure virtual machine through the browser.
FAQs
Q1. What is the difference between Azure Bastion and Cloud Shell?
Azure Bastion and Cloud Shell are both services provided by Microsoft Azure, but they serve different purposes. Azure Bastion is a fully managed service that provides secure and seamless RDP (Remote Desktop Protocol) and SSH (Secure Shell) access to Azure virtual machines without the need for public IP addresses or VPN connections. On the other hand, Azure Cloud Shell is an interactive command-line interface (CLI) environment that allows users to manage and interact with Azure resources directly from a browser, providing access to a preconfigured Linux or Windows shell with common tools and utilities.
Q2. Is Azure Bastion a proxy?
Azure Bastion can be thought of as a jump server or a gateway rather than a traditional proxy. It acts as an SSL/TLS encrypted, centrally managed entry point into Azure virtual machines, providing secure remote access using RDP or SSH protocols over the Internet. It eliminates the need to expose virtual machine ports directly to the public internet while ensuring a secure and auditable connection.
Q3. What is the difference between Azure Bastion and NAT Gateway?
Azure Bastion and NAT Gateway serve different purposes in Azure networking. Azure Bastion provides secure and direct remote access to Azure virtual machines, eliminating the need to expose public IP addresses or manage VPN connections. On the other hand, NAT Gateway is a network address translation service that allows outbound connectivity for resources within a private subnet in a virtual network. It enables resources in the private subnet to access the internet while using a static public IP address for communication, without exposing the private IP addresses to the public.
Q4. Does Azure Bastion require its own subnet?
Yes, Azure Bastion requires its own dedicated subnet within a virtual network. The subnet reserved for Azure Bastion must be separate from the subnets used by other resources in the virtual network. This separation ensures that the traffic to and from Azure Bastion is properly isolated and secured. When configuring Azure Bastion, it automatically deploys the necessary infrastructure components, including a subnet, to establish the secure remote access gateway.